SOCKS5 proxy
Connectivity Windows Linux macOS Desktop Feature
最近更新时间:
Using our SOCKS5 proxies can further minimize your computer's identity from being revealed and reduce CAPTCHAs. This guide explains why SOCKS5 is beneficial and how to use it.
What this guide covers
- Overview
- Why the proxy is beneficial
- - Kill switch
- - Reduced CAPTCHAs
- - Static IPv6 / IPv4 addresses
- How the proxy works
- Get started with the SOCKS5 proxy
- Testing the connection
- WireGuard and SOCKS5
Overview
With the SOCKS5 proxy on all of Mullvad's VPN servers, you can further minimize your computer's identity from being revealed. This simple yet powerful feature also reduces CAPTCHAs.
For advanced users, the proxy is located on IP 10.8.0.1 (OpenVPN) or 10.64.0.1 (WireGuard), port 1080.
Why the proxy is beneficial
Kill switch
You may already be familiar with the Mullvad app's built-in "kill switch" safety feature. In other words, in the event that the Mullvad connection is terminated, all of your Internet traffic is automatically blocked, ensuring that your traffic is not accidentally leaked outside of our secure tunnel.
However, what happens if you've forgotten to start the Mullvad app? This is where using the SOCKS5 proxy comes in handy, to act as back-up protection.
Reduced CAPTCHAs
Another benefit is a reduction in the amount of CAPTCHAs you will experience. Many websites and services require this identification when they detect traffic that originates from a VPN server. The proxy makes this detection more difficult.
Static IPv6 / IPv4 addresses
Each Mullvad server can have multiple exit IPs, but if you use the SOCKS5 proxy on the server then you will always get the same IP-address - that of the proxy. This can be useful if you need to whitelist your Mullvad IP somewhere. The proxy provides you with an IPv6 address and an IPv4 address. You can find them on our Connection Check page.
How the proxy works
If you configure your browser, for example, to use the SOCKS5 proxy, it will direct all of your internet access via the proxy which is only accessible through Mullvad. So if you haven't turned on the app, your browser will prevent all internet access and therefore won't leak any information.
The proxy also works with routers and any other VPN used together with Mullvad's servers.
Get started with the SOCKS5 proxy
Follow these steps to configure your web browser to use our SOCKS5 proxies.
Firefox
- In a Firefox browser window, click the menu button in the top right corner and choose Settings.
- In the search box, type “network”, then click on the Settings button in the result.
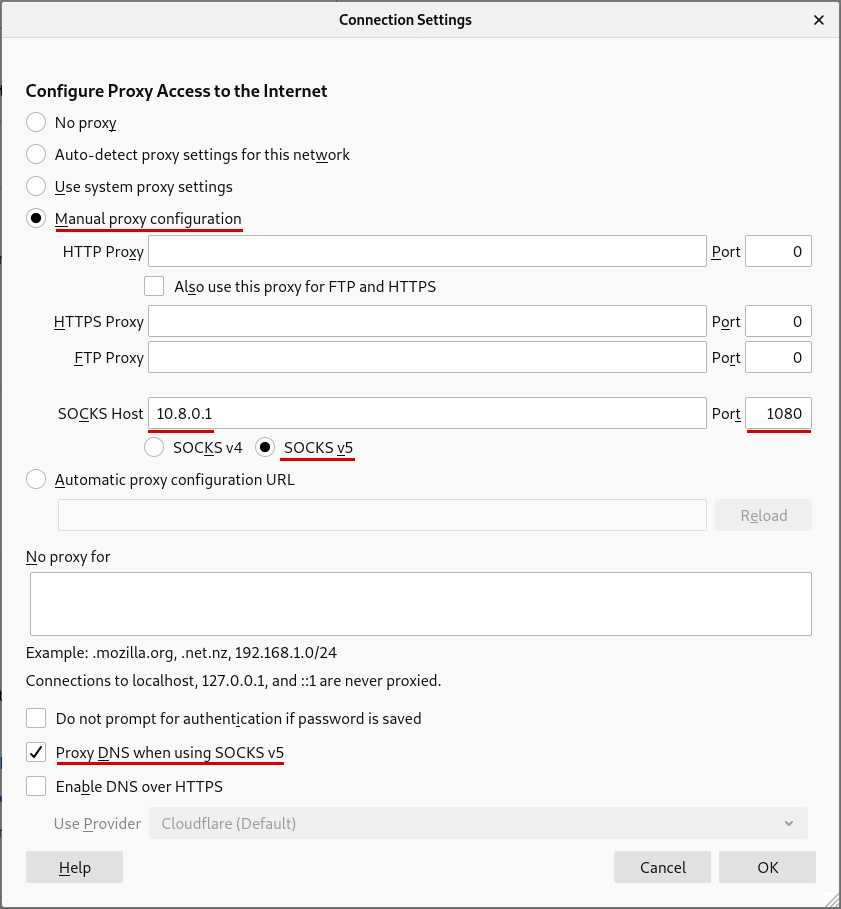
- Select Manual proxy configuration.
- Make sure that the HTTP Proxy and HTTPS Proxy fields are empty.
- In the SOCKS Host field, enter 10.8.0.1 and enter 1080 in the Port field.
- Click on SOCKS v5
- To prevent DNS leaks you can enable Proxy DNS when using SOCKS v5. However note that the DNS content blockers in the Mullvad app won't work if you enable this setting.
- Click on OK.
To disable SOCKS5, go to step #3 and change the setting to No Proxy.
Accessing local network services
If you need to access services on local network servers then use the text area which says No proxy for below the SOCKS settings. Enter your addresses like for example https://192.168.1.1 there. Remember to also enable Local network sharing in the Mullvad app settings.
Android - Firefox
Note: The about:config settings page was removed from Firefox on Android and they are currently only available in Firefox Nightly (the development version of Firefox).
- Enter about:config in the address bar and click on Send.
- In the search field, enter proxy.
- Scroll down to network.proxy.socks and enter 10.8.0.1.
- Scroll down to network.proxy.socks_port and enter 1080.
- Change the value for network.proxy.socks_remote_dns to True.
- Change the value for network.proxy.socks_version to 5.
- Change network.proxy.type to 1.
- Clear the field for network.proxy.http.
- Clear the field for network.proxy.ssl.
- Click on the back button to save the changes.
To disable, go to step #7 and change the setting to 5.
Windows - Chrome / Brave
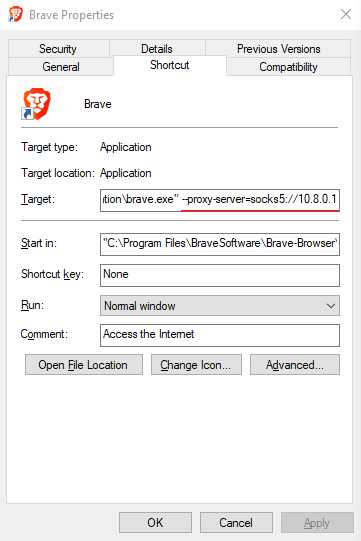
Right click on your desktop shortcut to Chrome or Brave and select Properties. Then add the following to the end of the Target (the field in the top) after the text that is already there. Make sure to first put one empty space after the current text and then add this:
When using WireGuard protocol:
--proxy-server=socks5://10.64.0.1
When using OpenVPN protocol:
--proxy-server=socks5://10.8.0.1
Then click on OK.
Windows - Edge
- Open the Windows Settings > Network & Internet.
- Click on Proxy in the left side.
- Enable Use a proxy server and set the address to
socks=10.8.0.1for OpenVPN protocol and set the port to1080. For WireGuard protocol set the address tosocks=10.64.0.1. - Click on Save.
Make sure that the settings are really saved by clicking on for example "Status" in the left side and then click on "Proxy" again. If you write https:// in front of the address it won't be saved. Windows adds that automatically.
Linux - Chromium
This works with Brave and other Chromium based browsers. Start it from a Terminal like so:
brave-browser --proxy-server=socks5://10.64.0.1
chromium-browser --proxy-server=socks5://10.64.0.1
For OpenVPN use 10.8.0.1 instead of 10.64.0.1 which is for WireGuard.
Note: The --proxy-server flag applies to URL loads only. There are other components of Chrome which may bypass the proxy server. To address this add the flag --host-resolver-rules="MAP * ~NOTFOUND , EXCLUDE 10.64.0.1".
macOS - Safari / Chrome / Edge / Brave
When using the Mullvad app you can enable the SOCKS5 proxy for Safari, Chrome, Edge and Brave. This only works when using the Mullvad app. Open the macOS System Preferences > Network and click on the active (green) Ethernet or Wi-Fi connection. Then click on Advanced... > Proxies and check "SOCKS Proxy" and then enter the following.
When using WireGuard protocol:
SOCKS Proxy Server:
10.64.0.1 : 1080
When using OpenVPN protocol:
SOCKS Proxy Server:
10.8.0.1 : 1080
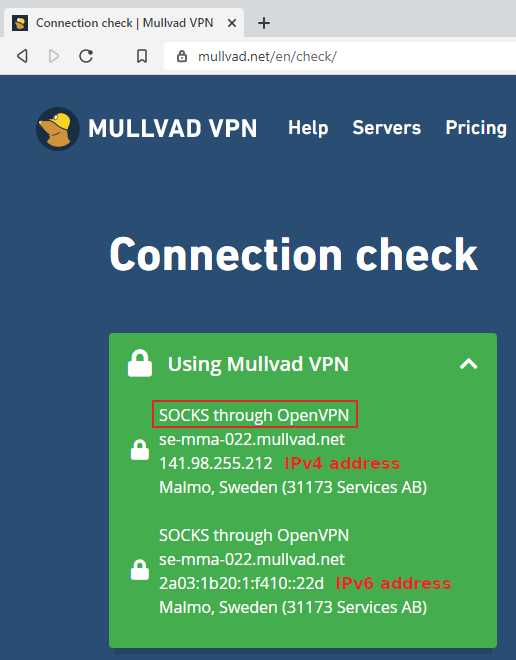
Testing the connection
Go to the Mullvad Connection Check to see if the web browser is using the proxy. Expand the top left box with the down arrow and look for the words "SOCKS through".
WireGuard and SOCKS5
All WireGuard servers have two SOCKS5 proxies listening on them:
- The SOCKS5 proxy on 10.64.0.1 with port 1080 which is not reachable from other WireGuard servers.
- The SOCKS5 proxy on 10.124.0.x to 10.124.1.x with port 1080 are reachable from other WireGuard servers. These IPs are unique for each WireGuard server. For instance, 10.124.0.4 is nl-ams-wg-001.relays.mullvad.net and 10.124.0.2 is se-mma-wg-001.relays.mullvad.net.
Multihop with SOCKS5
You can also use the SOCKS5 proxies to multihop. To do so, you can configure your browser or other program to exit from a server that is different from the one you connected to.
For instance, if you are connected to se1-wireguard.mullvad.net and then want to exit via nl1-wireguard.relays.mullvad.net, you would configure your browser/program to use nl1-wg.socks5.relays.mullvad.net on port 1080 as your exit node.
There are three options for using this:
- Use the Mullvad Browser Extension for Firefox to switch location easily.
- Use the Mullvad Browser which includes the Mullvad Browser extension.
- Set it up manually in Firefox. See the blog post SOCKS for expats.
You can also try this in a terminal (in the following examples, we are connected to se1-wireguard):
Without SOCKS5 proxy
Note that the Mullvad VPN server will assign one of multiple possible exit IPs.
curl https://am.i.mullvad.net 193.138.218.224
With SOCKS5 proxy on the connected Mullvad VPN server
Note that the proxy has a different exit IP. Each proxy has only one exit IP.
curl https://ipv4.am.i.mullvad.net --socks5-hostname 10.64.0.1 193.138.218.221
With SOCKS5 proxy running on a different Mullvad VPN server
Note that you will get the exit IP from the proxy on the other Mullvad VPN server.
curl https://ipv4.am.i.mullvad.net --socks5-hostname nl1-wg.socks5.relays.mullvad.net 193.32.249.131
With SOCKS5 proxy - IPv6 exit IP
Each proxy also has one IPv6 exit IP.
curl https://ipv6.am.i.mullvad.net --socks5-hostname 10.64.0.1 2a03:1b20:1:f410::a01d
"WireGuard" is a registered trademark of Jason A. Donenfeld.